A Regulator’s Guide to TRISA
This guide consists of a set of frequently asked questions that regulators have about TRISA. It is intended for informational and educational purposes and assumes that a regulator has limited knowledge of the Travel Rule and TRISA.
Contributors: Edwin Schmierer, Benjamin Bengfort, Ph.D., Rebecca Bilbro, Ph.D., Patricia Morelli, Lorraine Ratchford, Simone Martin, Samantha Pelosi, Samuel Jacques-Cloutier, John Jeffries
Please send feedback to [email protected]. Last updated: March 31, 2025.
1. What is the Travel Rule and why is it important?
In October 2018, the Financial Action Task Force (FATF), the international anti-money laundering (AML) and terrorist financing watchdog, brought Virtual Asset Service Providers (VASPs) within the global AML and Combating the Financing of Terrorism (CFT) umbrella with its interpretive notes to Recommendation 15 on New Technologies. VASPs are financial institutions that manage virtual assets including cryptocurrencies. This meant that VASPs had to assess money-laundering risk posed by counter-party VASPs. Just as traditional banks and financial institutions must comply with Know Your Customer (KYC) and Customer Due Diligence (CDD) regulations, Recommendation 15 extends AML and CFT to VASPs. Instead of KYC, it’s Know Your VASP (KYV).
In June 2019, FATF modified its Recommendation 16 to include Virtual Asset Service Providers (VASPs). Under what is known as the “Travel Rule”, VASPs are required to share specific sender and receiver information for cross border cryptocurrency transactions over a set threshold. The Travel Rule is important as an AML and CFT regulation. It is designed to help law enforcement and regulatory authorities investigate suspicious transfers and illicit proceeds.
2. What is a VASP?
VASPs are financial institutions that manage virtual assets such as cryptocurrencies. A non-exhaustive list of different types of VASPs include:
- Centralized Exchange
- Decentralized Exchange
- Person-to-Person Exchange
- Crypto ATM Operator
- Custody Provider
- OTC Trading Desk
- Investment Fund (hedge fund, family office, ETF)
- Token Project
- Gambling or gaming site
- Mining Pool
- Mixing Service
It is important to note that TRISA membership is open to a wide range of institutions including Virtual Asset Service Providers (VASPs), Crypto Asset Service Providers (CASPs), Money Service Businesses (MSBs), traditional financial services institutions, and regulatory bodies.
3. What is TRISA?
The Travel Rule Information Sharing Alliance (TRISA) is a professional working group of VASP operators, Travel Rule solution providers, regulators, advisors, and technical implementers dedicated to making cross-border exchanges of cryptocurrencies safe and lawful. TRISA consists of four components including:
- The TRISA Working Group, a 501(c)(6) professional organization
- A white paper and open source code that describes a protocol for an open source, interoperable, and decentralized messaging layer for Travel Rule compliance
- The Global Directory Service is network of trusted VASPs, where TRISA acts as the certificate authority that issues identity certificates to verified counterparties
- Envoy, an open source messaging service built to help compliance teams handle travel rule exchanges efficiently and securely using the TRISA or TRP protocols
TRISA’s source code is open source and available via its Github repository along with comprehensive documentation. TRISA’s mission is animated by its Guiding Principles:
- Open Architecture: TRISA is committed to interoperability with open security standards and different messaging protocols.
- Open Source: TRISA goes beyond being open and is open source. VASPs large and small have access to TRISA’s source code on Github. VASPs can inspect, download, modify, and implement TRISA at no cost.
- Secure: TRISA applies the proven Certificate Authority (CA) model, commonly used in e-commerce transactions and government communications.
- Private: TRISA employs Public Key Cryptography (PKC) to ensure personally identifiable information (PII) remains private and is encrypted in flight and at rest.
- Decentralized: TRISA’s peer-to-peer network adheres to the ethos and benefits of blockchain technologies, eliminating single points of failure and ensuring a resilient and secure network.
- Reliable: TRISA requires mutual authentication, meaning counter-parties have to prove their identity before exchanging information.
4. What is the TRISA white paper?
The TRISA white paper describes an open source, interoperable, and peer-to-peer protocol for Travel Rule compliance. The white paper has been implemented in the form of a Remote Procedure Call (RPC) specification for inter-VASP communication, and a reference library implemented in the Go programming language. TRISA has also implemented and hosts a Global Directory Service (GDS), which facilitates a network of TRISA-verified VASPs as a Trusted VASP Certificate Authority (see below). TRISA maintains open source Github repositories available to VASPs as they build, test, and deploy their TRISA node into production. In addition to the open source repositories, TRISA maintains documentation for implementation and a TestNet with robot VASPs and demos. The white paper is reviewed and updated proactively by TRISA’s Technical Subcommittee to address changes in regulations and operator needs.
5. What is the TRISA Global Directory Service (GDS)? What is Envoy? How are they different?
TRISA’s Global Directory Service (GDS) is a network of verified VASPs. The purpose of the GDS is to facilitate peer-to-peer exchanges between TRISA members by: (1) issuing mutual Transport Layer Security (mTLS) certificates to verify exchanges; (2) providing discovery services for finding TRISA endpoints; and (3) providing certificate and KYC information for verification. When a VASP registers with the GDS, TRISA will validate the VASP and then issue x.509 identity certificates for the Testnet and/ or Mainnet networks. It’s important to note that the GDS consists of two different networks: Testnet and Mainnet. Each network requires a unique identify certificate for secure communication. Currently, the TRISA organization hosts the GDS on behalf of the TRISA network.
Envoy is an open source secure messaging service that allows VASPs to exchange travel rule data (IVMS101 standard) using the TRISA or TRP protocols. Envoy makes it easy for compliance teams to use the TRISA or TRP protocols for secure, P2P messaging. Envoy consists of a user interface, a REST API, and TRISA and TRP endpoints. Compliance teams can think of Envoy as a secure “email inbox” for exchanging PII. Engineering teams have the ability to use the API for programmatic interactions or to integrate into a product. Envoy is available to implement DIY or as a managed service through Rotational Labs, TRISA’s technical implementation partner.
To use the TRISA protocol, VASPs must first register with TRISA’s GDS. Then, they can set up Envoy with the identity certificates issued by TRISA.
6. Is TRISA decentralized?
Yes, TRISA’s network is decentralized. TRISA is a peer-to-peer (P2P) to network of trusted counter-parties seeking to securely exchange Personally Identifiable Information (PII) to comply with the Travel Rule. TRISA’s protocol enables VASPs to communicate directly with each other and not through a centralized hub.
However, TRISA centralizes a small component of the protocol by acting as a certificate authority, issuing identity certificates for authentication and verification of VASPs. This allows VASPs to understand exactly who the counter party is and what their compliance requirements are.
7. How does TRISA promote Travel Rule compliance?
TRISA is a global, open source, interoperable, and peer-to-peer Travel Rule solution. With TRISA, VASPs can host their own TRISA node (server) to securely exchange Travel Rule data packets. These packets are exchanged directly with each other to comply with Travel Rule regulations. Travel Rule data is encrypted in flight and at rest using secure envelopes. It is important to note that TRISA is a peer-to-peer network. There is no centralized authority collecting or exchanging Travel Rule data.
8. Who can join TRISA?
TRISA is open to organizations that offer virtual asset or digital asset services. Organizations must have a legitimate business purpose to join TRISA. Member organizations may be:
- Virtual Asset Service Providers (VASPs)
- Crypto Asset Service Providers (CASPs)
- Money Service Businesses (MSBs)
- Traditional financial services institutions
- Regulatory bodies
9. How does a VASP become a TRISA-verified VASP?
VASPs must complete a formal registration and due diligence process by TRISA that includes physical and digital verification of the VASP. The verification process follows FATF’s Recommendations for VASP licensing and registration. The process is designed to be thorough and rigorous, but not financially burdensome for VASPs to complete on their own. It does not require a third-party auditor or hefty fees. TRISA verifies all data submitted by VASPs and conducts sanctions checks.
The initial validation of a VASP includes verification of business identity, regulatory jurisdiction, control over URLs and email addresses, and risk ratings. The TRISA Working Group worked with VASPs and the Global Digital Finance (GDF) Working Group to develop a VASP verification questionnaire, called the Travel Rule Information Exchange (TRIXO) Questionnaire, that applies across various protocols and technical implementations. This questionnaire is designed to help the TRISA Working Group and TRISA members understand the regulatory regime of a VASP. The information ensures that required compliance information exchanges are conducted correctly and safely.
Once verified, TRISA issues a validated X.509 certificate to the VASP. The validated X.509 certificate contains public and private key pairs that VASPs use to protect their communications with peers by encrypting the communications channel. X.509 certificates are commonly used for e-commerce and governmental communications.
Once verified, a VASP can choose to set up and run their own TRISA node using the open source resources (DIY) or use a commercial Travel Rule solution. All TRISA-verified VASPs have the responsibility to communicate securely, maintain their system, and protect the integrity of the network.
10. What Travel Rule solutions exist in the market?
There are several open source and commercial solutions available to facilitate Travel Rule compliance.
Open Source Solutions
- TRISA
- Travel Rule Protocol (TRP)/ OpenVASP
Commercial/ Closed Solutions
- Sygna Bridge
- 21 Analytics
- NotaBene
- CoinBase TRUST
- VerifyVASP
TRISA is currently interoperable with TRP/ OpenVASP and Sygna Bridge. TRISA is working toward interoperability with other solutions.
11. How do you know if a VASP is a member of the TRISA network? How do I know if a VASP is Travel Rule compliant?
The easiest way to determine if a VASP is a TRISA member is to look up the VASP in TRISA’s Global Directory Service. To do so, you will need to know the VASP’s TRISA Endpoint or Common Name (see below). Contact the compliance officer at a VASP in your jurisdiction to determine if the VASP is Travel Rule compliant.
12. What is a TRISA Endpoint and/or Common Name?
A TRISA Endpoint is a server address (e.g. trisa.myvasp.com:443) at which the VASP can be reached via secure channels. You can think of it as a secure phone number to send and receive sensitive data. TRISA uses public key cryptography to secure endpoints. The Common Name typically matches the Endpoint, without the port number at the end (e.g. trisa.myvasp.com) and is used to identify the subject in the X.509 certificate.
13. How does TRISA help regulators?
TRISA helps regulators on three different levels.
First, on a leadership level, TRISA is a global community that promotes Travel Rule compliance and welcomes participation from regulators across different countries and jurisdictions. As the cryptocurrency markets continue to grow and evolve, TRISA is an inclusive and diverse venue for regulators to work with VASPs, lawyers, technologists, and solutions providers to make cryptocurrency markets safe and lawful.
Secondly, on a strategic level, TRISA offers a turnkey solution that countries and jurisdictions can adopt to promote Travel Rule compliance. TRISA’s Guiding Principles mean the protocol and solution are accessible, interoperable, secure, private, and reliable across countries and jurisdictions.
Finally, on an operational level, TRISA facilitates compliance with the Travel Rule and ensures regulators have access to the data they need in the event of a financial crimes investigation. When there is a financial crimes investigation that includes a TRISA-verified VASP, the VASP will be able to produce the Travel Rule data required by law. The data will be securely stored by the VASP or a third-party Travel Rule solution provider. TRISA ensures that both counterparties are complying because both counterparties exchange a signed envelope with matching digital signatures for the transaction. This proves that neither counterparty tampered with the secure envelopes since the original transmission of the Travel Rule data packet. This provides evidence of non-repudiation, which in this case is cryptographic proof that both parties have identical compliance information exchanged at the time of the transaction.
14. What can you do to advance Travel Rule compliance in your jurisdiction?
The first step is to educate fellow regulators and colleagues on the similarities and differences between cryptocurrencies and fiat. The TRISA Working Group offers a forum for discussion. At the same time, crypto risk intelligence companies issue periodic reports on AML and cryptocurrency crime. Second, if Travel Rule regulations are not in force in your jurisdiction, advocate for it as an important AML and CFT tool. Third, work with VASPs in your jurisdiction to ensure they are Travel Rule compliant.
15. What happens when a VASP in my jurisdiction wants to transact with a VASP in another jurisdiction that has not implemented the Travel Rule?
This is known as the sunrise issue, whereby regulations are rolled out unevenly across the world. Any VASP can apply to become a TRISA-verified VASP, even if they operate in a jurisdiction that does not enforce the Travel Rule. If the counter-parties are both TRISA members, they can transact and be in compliance. In the event that the counter-party VASP is not a TRISA member or does not use a third-party Travel Rule solution, then the transaction may not be in compliance with the Travel Rule.
16. What type of reporting or monitoring does TRISA offer for regulators?
TRISA does not provide reports, analysis, or monitoring for regulators. TRISA is a peer-to-peer network. There is no central organization collecting, analyzing, or monitoring transactional information. This is an intentional network design choice meant to promote security since a central authority would be identified as a honeypot of valuable data and potentially targeted by bad actors.
TRISA provides a means for vetted VASPs to securely exchange Travel Rule information and ensures VASPs have the compliance data needed by regulators in the event of a financial crimes investigation.
17. How does TRISA work? What’s a high-level technical description of the system?
TRISA uses a trusted Certified Authority (CA) model, adopted from the International Organization for Standardization (ISO) and used to secure most e-commerce and governmental communications, to actively verify the identity of VASPs. Certificate authorities offer a root of trust to anchor identities to a chain of trusted entities. The architecture catalogs verified VASPs’ public key addresses, which can be used to open a secure line of communication between VASPs to transmit users’ Personally Identifiable Information (PII). The CA model safeguards against a single point of failure, provides protection from attacks, and is scalable to accommodate the growing crypto landscape.
18. How does TRISA facilitate secure exchanges and data security?
TRISA promotes the use of secure exchanges both: (1) in flight using mutually authenticated TLS (mTLS) version 1.3; and (2) at rest through the use of multi-layer data cryptography. Secure Envelopes that contain compliance information are encrypted twice. The message payload itself is encrypted and digitally signed using a per-envelope secret shared between VASPs. The secret itself is encrypted using public key cryptography so that only the recipient of the secure envelope can decrypt the entire payload. The shared secret provides non-repudiation since timestamps are digitally signed, meaning it is possible to cryptographically prove that both parties have identical compliance information exchanged at the time of the transaction. Further, data can be erased when it no longer needs to be maintained for compliance purposes simply by deleting the private keys that decrypt the envelopes, making it no longer possible to open the secure payload. This process is called “Erasure”. A final benefit to secure envelopes is that they are amenable to long-term storage so that VASPs can retain encrypted compliance data in accordance with data retention laws required by their jurisdiction (e.g. 5 or 7 years).
19. What data is exchanged in a secure envelope?
The data includes: (1) identity information; and (2) transaction information. For identity, TRISA uses the interVASP Messaging Standard (IVMS101), an internationally recognized standard that helps with language encodings, numeric identification systems, phonetic name pronunciations, and standardized country codes (ISO 3166). The Originator VASP needs to encrypt and send two pieces of data in IVMS101 format: Originator customer data and Originator VASP data. The transaction details sent include sender/originator, intended recipient, transaction amount and other information used to identify the transaction on the blockchain. As stated above, the data is encrypted twice in the secure envelope.
20. How does TRISA protect the privacy of users?
Privacy is core to TRISA’s protocol and TRISA maintains the privacy of senders and receivers. Privacy is especially important with cryptocurrency transactions because it is possible to publicly view the balance of a wallet address. A wallet address is a string of digits in a specific format that is recognized by the cryptocurrency’s network (e.g. Bitcoin or Ethereum) and is used to receive transactions. Wallet addresses are often shared publicly so people know where to send funds. To gain access to the funds or tokens in a wallet address, the user must have the private key for the address.
This is an important difference between fiat transactions and cryptocurrency transactions. With fiat transactions, it is not possible to view a user’s bank account. In contrast, crypto transactions often involve sharing a wallet address to receive funds. Each blockchain network such as Bitcoin and Ethereum has its own block explorer that provides data, including balances, of wallet addresses. Examples of block explorers are Blockchain.com for Bitcoin and Etherscan.io for Ethereum.
This means that if a bad actor looks up the balance of a wallet address and later obtains the personally identifiable information (PII) of the address owner, the bad actor can physically threaten or harm the wallet owner in an effort to obtain the private key to assume control over the wallet and the funds. As a result, the risk of physical harm to users is significantly increased if PII data is not sufficiently protected.
TRISA is designed to protect the PII of the sender and receiver by using mTLS authentication and secure envelopes, which provide multi-layer encryption. Before transmitting data, a secure communications channel is opened between counter-parties. The secure envelope containing the compliance information that is sent to the counter-party is encrypted twice. Only the receiver can decrypt and access the data.
21. I’d like a compliance walkthrough. Can you show me a system diagram on how TRISA works?
The following diagram illustrates the encryption and transmission process for Travel Rule compliance data in a sample exchange. TRISA uses secure envelopes.
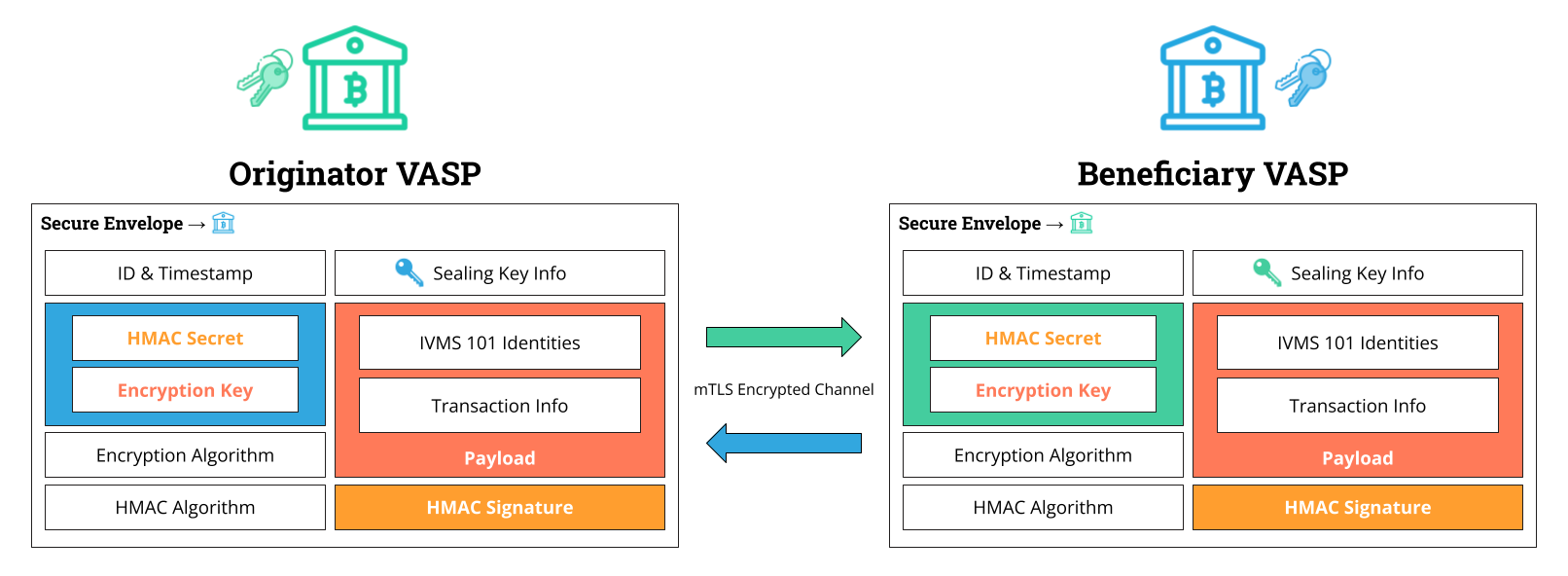
The sample exchange happens as follows:
| Step | Originator VASP | ||
| 1 | The Originator VASP finds the TRISA endpoint address and public identity key of the Beneficiary VASP. | ||
| 2 | The Originator VASP encrypts the sender’s data (using IVMS101 identity standard) and the transaction details using an encryption key. | ||
| 3 | The Originator VASP creates a Secure Envelope containing the encrypted payload, the encryption key and HMAC secret, and a timestamp, sealing it with the Beneficiary’s public identity key. | ||
| 4 | The Originator VASP opens an mTLS connection to the Beneficiary VASP’s TRISA endpoint and transmits the Secure Envelope via a TRISA Transfer message. | ⇨
Step |
Beneficiary VASP |
| 5 | The Beneficiary VASP receives the Secure Envelope via the mTLS connection and opens it using their private identity certificate. | ||
| 6 | The Beneficiary VASP validates the encryption key with the HMAC secret. | ||
| 7 | The Beneficiary VASP uses the key to decrypt the identity payload | ||
| 8 | The Beneficiary VASP stores the Originator VASP and sender details in a secure location for Travel Rule compliance. | ||
| 9 | The Beneficiary VASP encrypts the recipient’s data and Beneficiary VASP data and creates a secure envelope to send back to the Originator VASP. | ||
| Step | Originator VASP | 10
⇦ |
The Beneficiary VASP opens an mTLS connection to the Originator VASP’s TRISA endpoint and transmits the Secure Envelope via a TRISA Transfer message. |
| 11 | The Originator VASP opens the Secure Envelope, decrypts the payload, and stores the receiver and Beneficiary VASP details securely for Travel Rule compliance. |
22. How can a regulator confirm that the Originator VASP actually sent the Travel Rule data to the Beneficiary VASP?
Regulators can request that the VASP produce the secure envelope for the exchange. Secure envelopes have timestamps and a payload that is digitally signed by an HMAC secret. The digital signature proves that the data has not been modified. For complete proof, the regulator or VASP would then go to Beneficiary VASP and request proof of receipt of the secure envelope and if the digital signatures match, then it proves that the exchange occurred because cryptographically there is no way for one counterparty or the other to change that data without altering the signature.
23. Can a Regulator set up its own TRISA node or server for compliance purposes?
Yes, a regulator could set up a TRISA server for compliance purposes. For example, a regulator could require VASPs to send over secure envelopes every 90 days. In this scenario, the secure envelope would be signed with the regulator’s key (not the counterparty’s key) to prove that the envelope was not tampered with. The system could be configured to omit PII data. It would simply prove that the secure envelope was never altered or tampered.
24. Is it possible to simulate a transaction using sample transactions or scenarios or use it in a sandbox environment?
Yes. In addition to the Production TRISA Network, TRISA has also established a TestNet to enable demonstrations of the TRISA peer-to-peer protocol. TestNet hosts “robot VASP” services to facilitate TRISA integration. To view a demonstration of the TestNet illustrating TRISA interactions between “robot” VASPs on TestNet, visit vaspbot.net.
25. What is the TestNet and MainNet? Why are they different?
The TestNet is a sandbox environment that allows VASPs to test securely sharing the cryptocurrency transaction details required to meet the FATF Travel Rule requirements. The TestNet includes “robot” VASPs that give users the ability to interact with the TestNet by simulating transactions to see how secure transactions are conducted. Once a VASP completes testing, the VASP can request a certificate for MainNet, where live transactions take place. It’s important to note that the reason that there are two networks is because those networks are issued from different intermediate certificate authorities. A VASP that has been issued a TestNet certificate cannot connect to a node that is running on MainNet and vice versa. In other words, the MainNet certificate authority will not recognize TestNet certificates.
26. Does TRISA apply to Bitcoin only?
TRISA is chain-agnostic, meaning it applies to all cryptocurrency transactions regardless of the type of virtual currency or blockchain database used for the transaction.
27. Do Travel Rule packets get written to the blockchain?
No, Travel Rule packets do not end up on a blockchain. It is important to note that TRISA is a messaging layer that sits on top of blockchains. VASPs are expected to retain encrypted Travel Rule data in their own storage systems or with their third-party Travel Rule solution provider, according to their local data retention laws.
28. Where are the TRISA Global Directory Service’s servers located?
The servers that host the Global Directory Service are currently located in three regions: U.S., EU, and Singapore. The servers are decentralized and geo-replicated to ensure that the GDS is consistent, available, and fault-tolerant. TRISA plans to expand to more regions in the near future.
29. If TRISA is the Trusted VASP Certificate Authority that issues identity certificates to VASPs, can TRISA be compromised? Can a bad actor gain access and issue itself a certificate?
TRISA is the root certificate authority that issues certificates to VASPs after validation. TRISA works with Sectigo, one of the world’s leading cybersecurity providers of digital identity solutions including TLS certificates, to ensure certificates are authentic and trusted. TRISA does not maintain any private key material; only Sectigo does. Sectigo works with government agencies, research universities, and leading brands such as Vanguard and Intel to provide the highest trust level for their digital products and services.
30. What is a TRISA Service Provider (TSP)?
A TRISA Service Provider (TSP) is an organization that manages TRISA membership and certificates on behalf of its clients. By joining TRISA, TSPs can provide TRISA support into open source and commercial travel rule offerings, and provide VASP validation services in local or global markets. TSPs can also create interoperability with regional or private travel rule systems, using TRISA as an interoperability or VASP identity bridge.
Glossary of Terms
- AML: Anti-money Laundering (AML) refers to laws and regulations intended to stop criminals from disguising illegally obtained funds as legitimate income.
- Block explorer: A website or search tool that allows one to browse through blocks, view wallet addresses, network hash rate, transaction data and other key information on a blockchain network.
- Certificate Authority: An organization that issues digital certificates only after it has independently validated the identity associated with the certificate.
- Certificate: A verifiable small data file that contains identity credentials to help websites, people, and devices represent their authentic identity.
- CDD: Customer Due Diligence (CDD) is the process used by financial institutions to collect and evaluate relevant information about a customer.
- Github: An online hosting service that stores code on behalf of organizations.
- HMAC: Hash-based Message Authentication Code (HMAC) is a cryptographic authentication technique that uses a hash function and a secret key.
- IVMS101: A standard that defines a universal common language for communication of required originator and beneficiary information between VASPs. IVMS is published and maintained by The Joint Working Group on interVASP Messaging Standards (JWG).
- KYC: Know Your Customer (KYC) is similar to CDD and commonly used in traditional finance.
- KYV: Know Your VASP (KYV) is similar to CDD except applied to decentralized finance.
- mTLS: mutual Transport Layer Security (mTLS) is a mechanism for mutual authentication between services or servers. Also known as two-way authentication, it ensures that the parties at each end of a connection are who they claim to be.
- Open Source Software: Open source software is code that is designed to be publicly accessible—anyone can see, modify, and distribute the code as they see fit. Open source software is developed in a decentralized and collaborative way, relying on peer review and community production.
- PKC: Public-Key Cryptography (PKC) involves a pair of keys known as a public key and a private key (a public key pair), which are associated with an entity that needs to authenticate its identity electronically or to sign or encrypt data. Each public key is published and is accessible while the corresponding private key is kept secret.
- RPC: Remote Procedure Call (RPC) is a request–response protocol. An RPC is initiated by the client, which sends a request message to a known remote server to execute a specified procedure with supplied parameters. It is similar to a telephone call, in which the caller must wait for the recipient to pick up before anything can be discussed.
- Server: A computer on a network that sends and receives data.
- Wallet: Software that runs on a blockchain which stores private and public keys as well as monitors and keeps all the transactions related to those keys on a blockchain. There are two types of wallets: un-hosted and hosted. An un-hosted wallet, also called a private or non-custodial or self-hosted wallet, means the owner of the wallet has complete control over the wallet by retaining the private key. A hosted wallet, also called a custodial wallet, means that a third party, typically a VASP, controls the wallet by retaining the private key for a customer.
- Wallet address: A string of digits in a specific format that is recognized by the cryptocurrency’s network (e.g. Bitcoin or Ethereum) that identifies a wallet and is used to receive transactions.
